Permissions Assignment
CBP assignments refer to the process of assigning roles and permissions to users within the CBP system. This allows CBP owners to manage user access and define what actions each user can perform, secure and efficient operation of the platform.
This guide will help CBP owners assign different permissions to CBP users and easily manage their roles and access.
Manage CBP Users Permissions Steps Guide
- Go to CBP Configurations in Settings:
- Go to the "Additional Role" section.
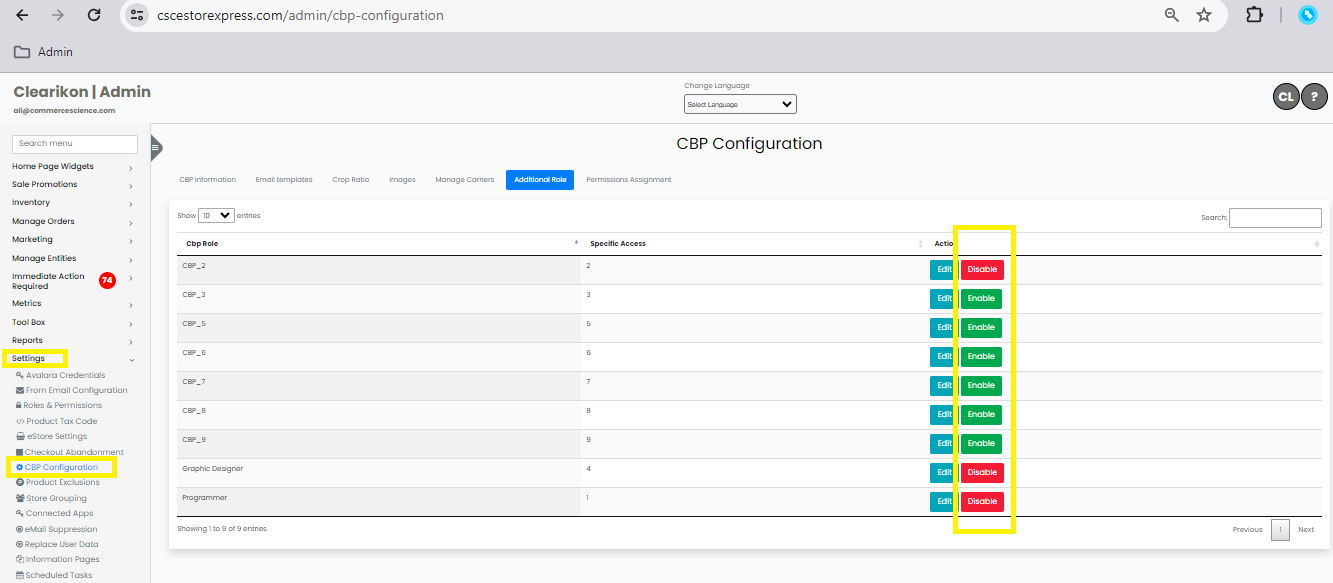
- Ensure the relevant role is enabled for managing permissions.
-
Note: You can also customize the name of the CBP role type for each user by clicking on the edit icon.
-
Now Navigate to "Permissions Assignment." (next to additional role tab) View the permissions for the relevant role.
Define Permissions:
Check or uncheck the boxes to define the permissions for that user.
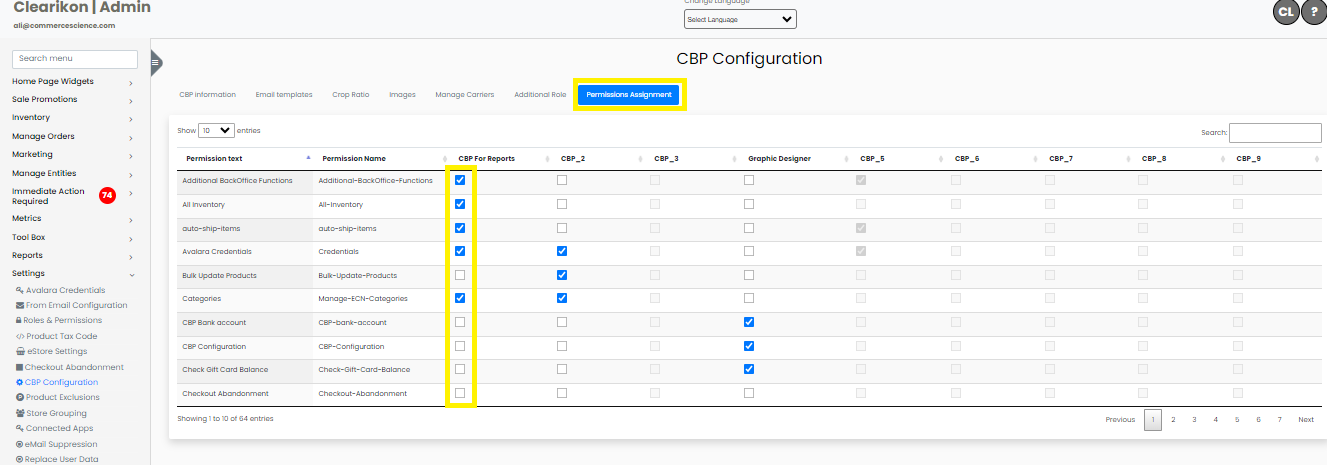
By following these steps, you can easily manage permissions within your CBP system.
To Create a New CBP User with an Additional Role
Navigate to the "Manage Entities" section. * Click on "Manage Users" * Click on the "Add User" button. * Fill in the user details as required. * Choose Role "CBP"
Choose Additional Access:
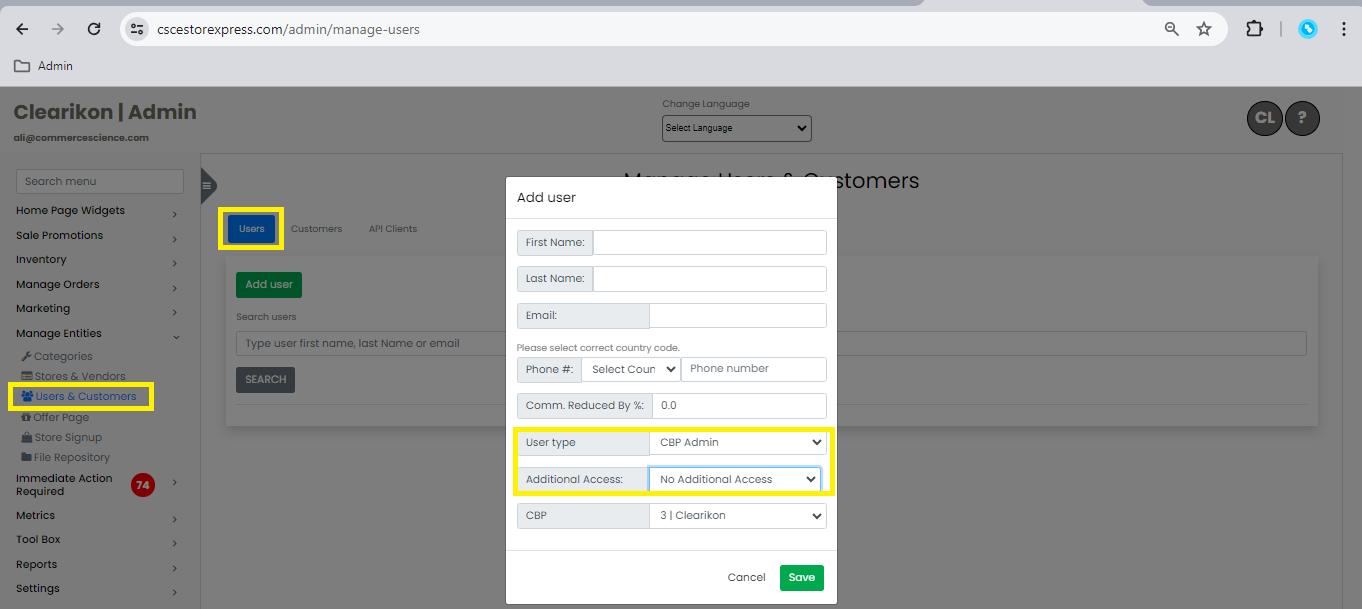
- Select the additional access for the CBP.
- Assign the roles that the new user should have.
Managing Existing CBP User Permissions
If you find the need to adjust the permissions for an existing CBP user, the process is easy. Begin by accessing the "Manage Users and Customers" section, where you can utilize feature to locate the specific user whose permissions require modification. Once you've identified the user, proceed to change their additional role to reflect the desired level of access.
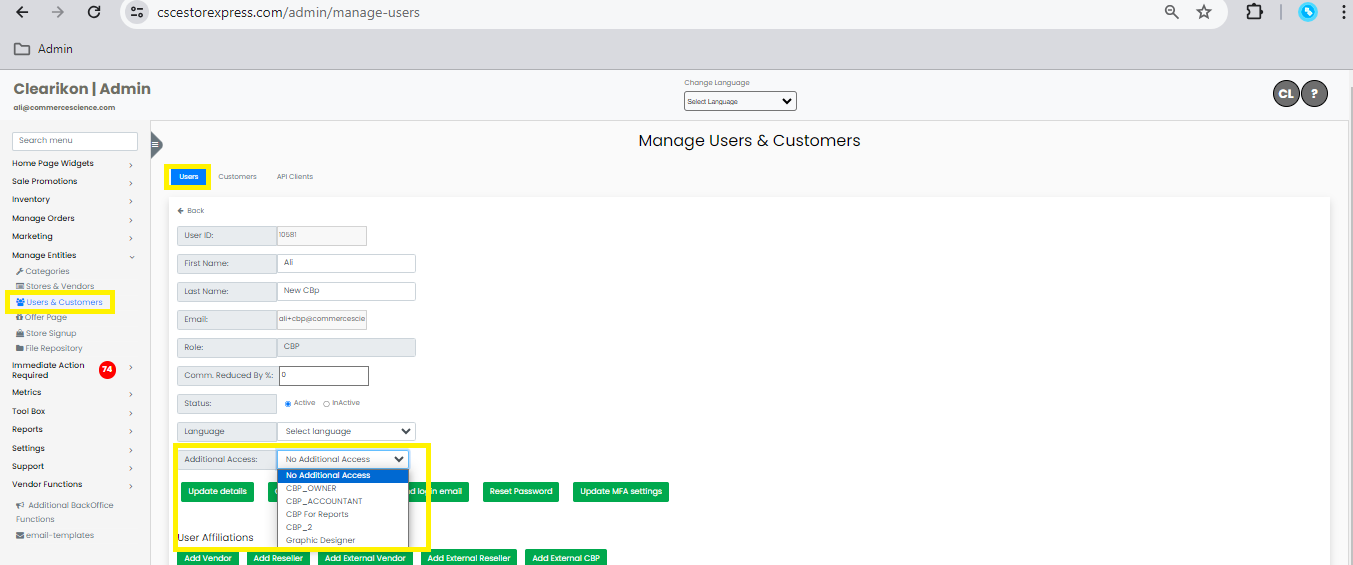
After adjusting the role, navigate to the "Permissions Assignment" section to fine-tune the cbp user's permissions by checking or unchecking the permission boxes. This process allows for efficient management of user access within the CBP system, ensuring that each user has appropriate permissions tailored to their role.